The Importance of Responsive Design: Why Your Website Needs to Adapt
In today’s fast-paced world, your website serves as the front door to your business. With an ever-growing array of devices from which people can access the internet—from smartphones to tablets, laptops to desktops—it is crucial that your website can adapt and provide an optimal experience across all these platforms.
This adaptability is where responsive web design comes into play. But what exactly is responsive design, and why is it vital for your business’s online presence?

What Is Responsive Web Design?
Responsive web design is an approach to web development that allows a website to fluidly change and respond to the size and capabilities of the user’s device. Whether someone visits your site from a small smartphone screen or a large desktop monitor, the site will automatically adjust to fit the screen size, orientation, and resolution. This adaptability is achieved through flexible layouts, images, and intelligent use of CSS media queries.
Why Responsive Web Design Is Important?
Improved User Experience
A responsive website offers a better user experience. Users can navigate your site with ease, regardless of their device. This ease of use leads to greater satisfaction, higher engagement, and increased conversion rates. For instance, a retail website that adjusts seamlessly across devices makes it easier for customers to browse and purchase products, directly impacting sales.
Increased Reach to Mobile Users
With over half of global web traffic coming from mobile devices, a responsive design can help you reach a wider audience. A mobile-friendly site is also more likely to retain visitors, as it offers them the convenience of accessing your site anytime, anywhere. For example, a local restaurant with a responsive website can attract more diners by making it easy for mobile users to find their menu, hours, and location.
Better Search Engine Rankings
Search engines like Google prioritize mobile-friendly websites in their search results. Responsive design is a critical factor in search engine optimization (SEO). It can help your site rank higher and become more visible to potential customers, which is particularly crucial for competitive industries where visibility can make or break a business.
Cost-Effectiveness
Maintaining separate sites for mobile and desktop users can be costly and time-consuming. Responsive design eliminates the need for multiple versions of your site, making it more cost-effective in the long run. This consolidation simplifies content management and updates, saving you time and resources.
Future Scalability
Responsive sites are designed to work across current and future devices. This future-proofing aspect means that as new devices (like smartwatches and IoT devices) enter the market, your responsive website is already prepared to meet these new challenges head-on.
The Drawbacks of Non-Responsive Websites
Poor User Experience
Non-responsive sites can frustrate users with tiny text, hard-to-click links, and the need to zoom in and out to read content. This frustration often leads to a high bounce rate as users leave in search of a more user-friendly site.
Limited Reach
You ignore a significant portion of the market by not accommodating mobile users. This limitation can result in lost opportunities, especially for businesses that rely on local search traffic.
Lower Search Engine Rankings
As mentioned, search engines favor mobile-friendly sites. A non-responsive design can lower search rankings, making it harder for potential customers to find your business online.
Higher Maintenance Costs
Running separate websites for mobile and desktop users is an outdated practice and more expensive. It requires more time for updates, double the hosting fees, and potentially twice as many design costs.
Take Action for a Better Website
If your business’s website isn’t responsive, it’s time to make a change. The online marketplace is evolving rapidly, and staying ahead means providing the best possible experience for your customers, regardless of how they access your site. Don’t let your website be the reason potential customers turn to competitors.
Contact us today for a free initial consultation about building a responsive website that looks great and performs exceptionally well across all devices. Let’s work together to create a website that adapts to your business and customers’ needs, ensuring you’re always one step ahead in the digital landscape.
Breaking Down the Benefits of Custom vs. Template Websites
Having a solid online presence is crucial for any business’s success. A website can serve as a place where customers can find answers at any time of day or as an always-open storefront. It is essential to invest in a platform that not only reflects your brand but also attracts and engages potential customers.
When creating a website, business owners often have to choose between using pre-made templates or opting for a custom-designed solution. Understanding the difference between the two and their advantages and disadvantages can help you make an informed decision for your business.

Understanding Website Templates
Website templates are predesigned layouts that allow users to quickly create a website by simply plugging in their content. These templates are readily available from various platforms and come with predefined designs, features, and functionalities.
Benefits of Template Websites
- Cost-Effective: One of the most significant advantages of website templates is their affordability. Since templates are pre-made and readily available, they typically come at a lower cost than custom-designed websites.
- Time-Saving: With templates, you can get your website up and running in hours or days, saving time that would otherwise be spent designing and developing a website from scratch.
- Ease of Use: Website templates are designed to be user-friendly, making them accessible to individuals with little to no technical expertise. You can customize the template by modifying colors, fonts, and images to suit your brand.
Drawbacks of Template Websites
- Lack of Uniqueness: One of the primary drawbacks of using a website template is the need for more uniqueness. Since templates are available to anyone, your website may look similar to countless others online, diluting your brand identity.
- Limited Customization: While templates offer some level of customization, they often come with restrictions on design and functionality. You may be unable to implement certain features or make significant design changes to align with your brand.
- Potential for Bloat: Most website templates come packed with features and functionalities that you may not need. This leads to bloated code and slower loading times, which can negatively impact user experience and SEO performance.
Understanding Custom Websites
On the other hand, custom websites are built from scratch by a developer. They are tailor-made to meet a business’s specific needs and requirements. Every aspect of the website, from design to functionality, is crafted to reflect the brand’s unique identity and goals.
Benefits of Custom Websites
- Unique Brand Identity: With a custom website, you have complete control over the design and aesthetics, allowing you to create a unique brand identity that sets you apart from the competition.
- Scalability and Flexibility: Custom websites are highly scalable and flexible. They can adapt to your business’s growth and evolving needs. You can integrate custom features and functionalities tailored to your specific requirements.
- Enhanced SEO Performance: Custom websites are optimized for search engines from the ground up, providing better control over on-page elements, site structure, and performance optimization, ultimately improving your SEO rankings and visibility.
Drawbacks of Custom Websites
- Higher Cost: Custom-designed websites typically have a higher price tag than template solutions due to the extensive design and development work involved.
- Longer Development Time: Building a custom website from scratch requires time and effort, as every aspect of the site needs to be created and implemented according to your specifications. This process may take longer than using a pre-made template.
- Dependence on Web Development Expertise: Unlike template websites, custom websites require the expertise of web designers and developers to bring your vision to life. This reliance on professionals may entail additional costs and coordination efforts.
Which Should You Choose?
While both template and custom websites have pros and cons, the decision ultimately boils down to your business’s unique needs and goals. While template websites offer affordability and quick deployment, they need more uniqueness and scalability for long-term success. On the other hand, custom websites provide unparalleled flexibility, branding opportunities, and SEO performance, making them a worthwhile investment for businesses looking to stand out in a crowded digital landscape.
If you are hiring a web designer, be sure to ask if they plan to use a template. Frequently, web designers have no experience building a website from the ground up. They rely on templates to build their websites, even though they often still charge as if the design is unique.
At 10T Web Design, we never use templates in our design. Even though every website is built from scratch, we do our best to have competitive pricing when compared to other designers using templates.
If you’re ready to enhance your online presence, contact us for a free initial consultation. 10T Web Design is here to help you build a custom website that reflects your brand identity and drives tangible business results.
Why WordPress is the Best Platform for Website Development

In today’s digital age, having a website is crucial for business success.
It serves as the online face of your brand, allowing you to reach a wider audience and connect with potential customers. However, building a website can be daunting, especially if you don’t have any coding experience. This is where WordPress comes in.
WordPress is a powerful content management system (CMS) that allows you to manage your website easily. Here are some of the benefits of using WordPress for website development.
Flexibility and Customization Options
WordPress offers a wide range of customization options. This allows you to create a website that reflects your brand’s unique personality. WordPress can be customized to meet your exact website needs with the assistance of a website developer.
User-Friendly Interface
WordPress has a user-friendly interface that makes it easy to manage your website’s content. You can easily add new pages, blog posts, images, and videos with just a few clicks. By managing routine updates yourself, you can save long-term on website maintenance.
SEO-Friendly Features
WordPress is designed with SEO in mind. It makes optimizing your website for search engines easy. It has built-in features like permalinks, meta descriptions, and XML sitemaps that help improve your website’s visibility in search engine results pages (SERPs).
Wide Range of Available Plugins and Themes
WordPress has a vast library of plugins and themes that allow you to add new features and functionalities to your website. Whether you need a contact form, social media integration, or e-commerce capabilities, there is a plugin or theme that can help.
Active Community Support
WordPress has a large and active community of developers and users who are always willing to help. Whether you need help troubleshooting an issue or want to learn more about a specific feature, you can find answers in the WordPress community.
Supported by Most Web Developers
It is estimated that roughly 43% of the websites on the Internet are powered by WordPress. Since WordPress is so widely used, almost any website developer can help you if something goes wrong with your current developer. Should the relationship goes south, you won’t be stuck with a website that no one else can update and maintain.
Examples of Successful WordPress Websites
WordPress isn’t just for small businesses! Many successful websites are built on WordPress, including businesses, blogs, and e-commerce stores. TechCrunch, The New Yorker, and even the Sony PlayStation Blog are all powered by WordPress, just to name a few. These websites demonstrate the effectiveness of WordPress in achieving business goals.
WordPress is the best and most widely used platform for website development. It offers a wide range of customization options, a user-friendly interface, SEO-friendly features, a vast library of plugins and themes, and active community support.
Looking to build a website that reflects your brand’s unique personality? Contact 10T Web Design for custom WordPress design services. We can help you create a website that stands out from the crowd.
Ten Tips for Creating and Executing a Successful Facebook Marketing Strategy

Facebook is one of the world’s most popular social media platforms, with over 2.8 billion active users.
As a result, it has become a crucial tool for businesses looking to reach new customers and engage with their existing audience. Here are ten tips for creating and executing a successful Facebook marketing strategy.
Define Your Audience
The first step in creating a successful Facebook marketing strategy is to define your target audience. Who are you trying to reach, and what are their interests and behaviors? Once you have a clear understanding of your audience, you can create content that resonates with them and tailor your ads to their specific needs.
Set Specific Goals
Before you begin your Facebook marketing campaign, it’s important to set specific goals. What do you want to achieve? How will you measure success? Whether it’s increasing brand awareness, driving website traffic, or generating leads, setting clear goals will help you stay focused and track your progress.
Create Compelling Content
To engage your audience on Facebook, you must create compelling content that grabs their attention. Your content can include blog posts, videos, images, and infographics. Be sure to keep your content relevant, informative, and visually appealing.
Use Facebook Ads
Facebook ads are a powerful tool for reaching new customers and promoting your brand. With Facebook’s advanced targeting options, you can reach people based on location, interests, and behaviors. Be sure to create eye-catching ads that grab attention and include a clear call to action.
Engage With Your Audience
Engaging with your audience is critical to building a solid presence on Facebook. Respond to comments, messages, and reviews promptly and professionally. This will help you build trust with your audience and show that you value their feedback.
Analyze Your Results
To determine the effectiveness of your Facebook marketing strategy, it’s important to analyze your results. Use Facebook Insights to track engagement, reach, and conversions. This will help you identify what’s working and what’s not, so you can make adjustments as needed.
Stay Consistent
Consistency is key when it comes to Facebook marketing. Be sure to post regularly and at the optimal times for your audience. This will help you stay top-of-mind and build a loyal following.
Don’t Overwhelm Your Audience
Posting too often on social media can drive an audience away. A few posts a week is usually enough to keep your audience’s attention without your posts becoming background noise. Evaluating your results helps determine if you are posting too often. Increasing your number of posts without increasing your audience engagement is a sign you should cut back.
Don’t Constantly Sell
Imagine watching TV and only getting commercials. Pretty soon, you will change the channel. If all of your posts are about directly selling to your audience, they will usually stop paying attention on Facebook, too. Instead, include content that provides value to your audience. Frequently asked questions, customer tips, or general industry news will help your audience see more than ads.
Monitor Your Competitors
Finally, watching your competitors and seeing what they’re doing on Facebook is important. Doing so will help you identify gaps in your strategy and stay ahead of the competition.
Creating and executing a successful Facebook marketing strategy requires planning, creativity, and analysis.
By following these tips, you can build a strong presence on Facebook and reach new customers more effectively.
Is it challenging to find time to execute an effective Facebook marketing campaign? Get in contact with us to manage your social media for you!
10 Reasons Your Business Needs a Website

- A professional website is crucial for any business in today’s digital age. It’s your online storefront and a reflection of your brand identity.
- Investing in a professional website not only helps you attract more customers but also improves your credibility and trustworthiness among them.
- A professional website can help you showcase your products and services effectively, making it easier for your potential customers to learn about your offerings.
- A well-designed website with easy navigation can enhance user experience and help visitors quickly find the information they need.
- A professional website can also help you establish your authority in your industry and stand out from the competition.
- A website with a responsive design can ensure visitors have a seamless experience regardless of the device they use to access it.
- With a website, you can have complete control over your online presence and make changes per your business needs.
- A website with an integrated blog can help you share valuable content with your audience and establish yourself as an industry expert.
- A professional website with strong call-to-action buttons can help you convert your visitors into customers.
- In short, a professional website is a must-have for any business that wants to establish a robust online presence, attract more customers, and grow its brand.
Keeping Your Passwords Safe and Secure

Your password is too short. Now it needs to include a number. Don’t forget to add a special character.
Passwords are frustrating to most people on the Internet. Balancing between something strong enough to keep you from getting hacked and easy enough to remember is tough.
Why are strong passwords important, and how can you keep track of them? Let’s look at some best practices to keep your accounts safe.
Your Email Password Is More Important Than You Think
I’m always surprised how most folks treat access to their email. “So what if they get my email password? It’s just my email.” That’s a phrase I seem to run across every time I discuss password security.
The truth of it is, if someone looking to do damage to you gains access to your email, they own you. Every account you have sends the password reset to your email. So, if a bad guy gains access to your email, they have access to your bank, credit card, and any number of other accounts.
Since your email gets tied to so many other accounts, your email password should be among the strongest you have and should never be reused anywhere else.
Speaking of reusing passwords…
Use a Different Password for Every Account
Brute force is one of the more common methods bad actors use when trying to steal credentials. Brute force involves guessing passwords randomly as fast as the system will allow in hopes of guessing correctly.
Most well-built websites will see someone attempting to brute force guess a password and will make efforts to stop them; usually, this is as simple as not letting them try for a short time. But, if you have an account on just one poorly coded website, it might not prevent someone from eventually guessing your password using brute force.
Having one account compromised is bad enough. If you reuse your password, having one compromised account means all your accounts are compromised.
Don’t Use Confidential Information
You might think that using a combination of some pseudo-personal information makes your password easy for you to remember. And you would be right. But it also makes your password far easier to guess.
If you are on social media, your birthday, your phone number, and the names of your spouse, children, and pets are trivial to find. However, even if you are not on social media, this information is still relatively easy to find.
Some people even use their social security number as a password, but the truth is, your SSN isn’t nearly as confidential as you think it is. Your social security number has likely already been part of a data breach, but if not, someone guessing your SSN-based password gives them both your password and your social security number.
Avoid Common Passwords
Whenever there is a data breach that includes passwords, I’m always amazed by how many people use very common passwords.
You might think you’re clever setting your password to ‘qwerty,’ but that’s been one of the top 10 most common passwords since we began using passwords. The same goes if your password is ‘123456,’ ‘password,’ or ‘princess.’
So, if you find your password on a list of most common passwords, it’s time to change it. If you use one of the passwords and someone tries guessing your password, these will be the first ones they try, and it’ll take far less than a second for them to run through the whole list.
Avoid Using Single Words
If you look at the most commonly used passwords above, you’ll notice that many of them are straight out of the dictionary. With just under half a million words in the English language, you might be left with the impression that an obscure word would make a good password.
But computers are quite fast, and if you give them a list (for instance, the dictionary), they can click through all the words in it pretty quickly. When you start guessing thousands of guesses every second, cranking through the dictionary takes only minutes.
Much like the brute force attack, this is one of the more common ways someone will try to guess your password. It’s (not so creatively) called a Dictionary attack.
Length Is More Important Than Complexity
A longer password is usually more difficult to guess than a shorter one, even when the shorter one is more complex because the total number of combinations multiplies with every character you add.
If you have a super complex, 6-character password (complete with uppercase, lowercase, numbers, and symbols), someone intent on guessing your password can try every combination in well under a day.
However, a 16-character, lowercase-only password would take several thousand millennia to guess every possible combination.
But Complexity Still Matters
Even though that 16-character, lowercase-only password is incredibly hard to guess, adding extra complexity to the password makes it virtually impossible.
I say “virtually” because it is still possible that someone gets lucky and guesses your password on the first attempt. But to guess it within a few years would take some winning-the-lottery-multiple-times-in-a-row luck.
If we add uppercase letters, numbers, and symbols to the 16-character password, we go from several thousand millennia to several million millennia to guess every combination.
Make Your Passwords Truly Random
The best password is one you can’t remember yourself. A genuinely random, 16-character password that includes upper- and lowercase letters, numbers, and special characters is incredibly hard to guess.
Don’t trust yourself to randomly pick your password because we’re all human and will fall into bad habits like selecting predictable patterns. Instead, you’ll be better off using a generator like passwords-generator.org.
They also have a nice feature that will not use similar characters (“Is that a zero or a capital O?”) and ambiguous characters (“What that a curly brace or a square brace?”). This relieves the frustration of figuring out if that character is a “1” or a lowercase “L” and doesn’t make your password significantly easier to guess.
And, while I can almost hear you ask, “If I can’t remember my password, how will I ever remember my password?” The answer is that you should…
Use a Password Manager
So, now you have genuinely random passwords unique to every one of your accounts, and you can’t remember any of them. So, how are you ever going to know your password?
You can use a password manager. There are several outstanding password managers out there. DashLane and 1Password, are among the best and only cost a couple of bucks a month.
Another option is the good, old-fashioned pen and paper. There’s nothing wrong with keeping all of your passwords in a notebook. (Address books work well, where you can put “Facebook” on the F page where you can easily find it later.) Just be sure to keep your password book in a safe place.
One method to stay away from is storing your passwords in a file on your computer. All it takes is a quick bit of malware, and every one of those once-secure passwords are compromised.
Setting Up K-9 Mail for Android
Looking to setup your email on your Android phone? This tutorial will walk you through the process.
Download K-9 Mail
First thing, if you haven’t already, download K-9 Mail from the Google Play Store.
Setup
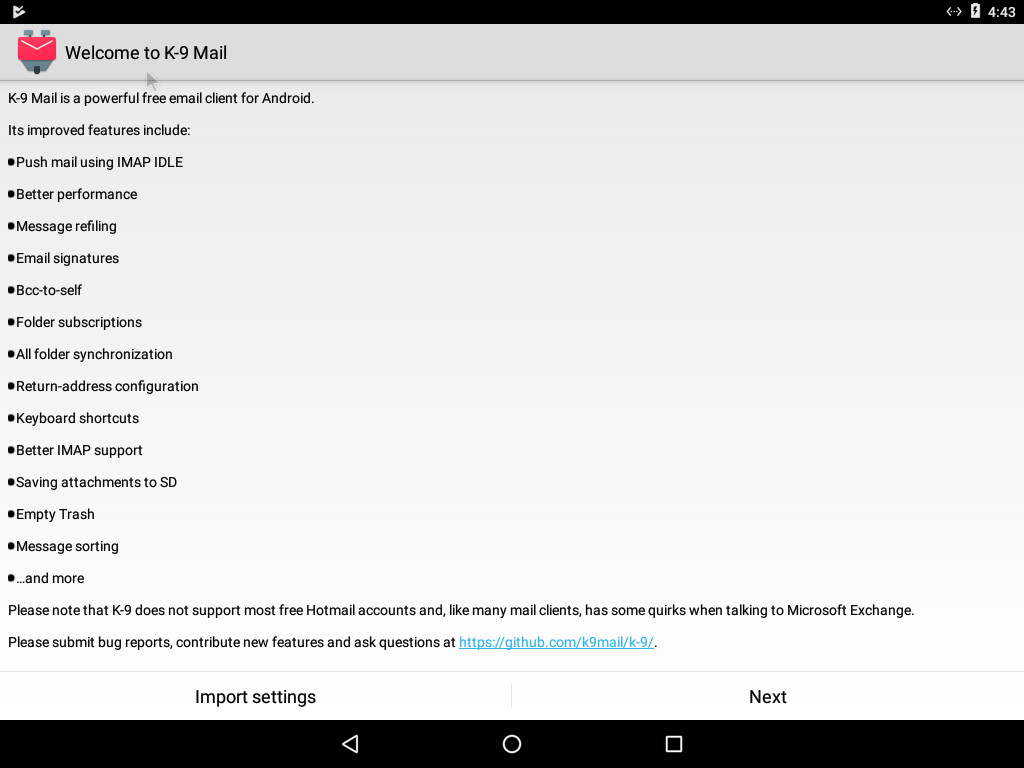
1) Once K-9 Mail installs, use the icon to open it up, and you should see a screen that looks like this, on which you can select “Next”.
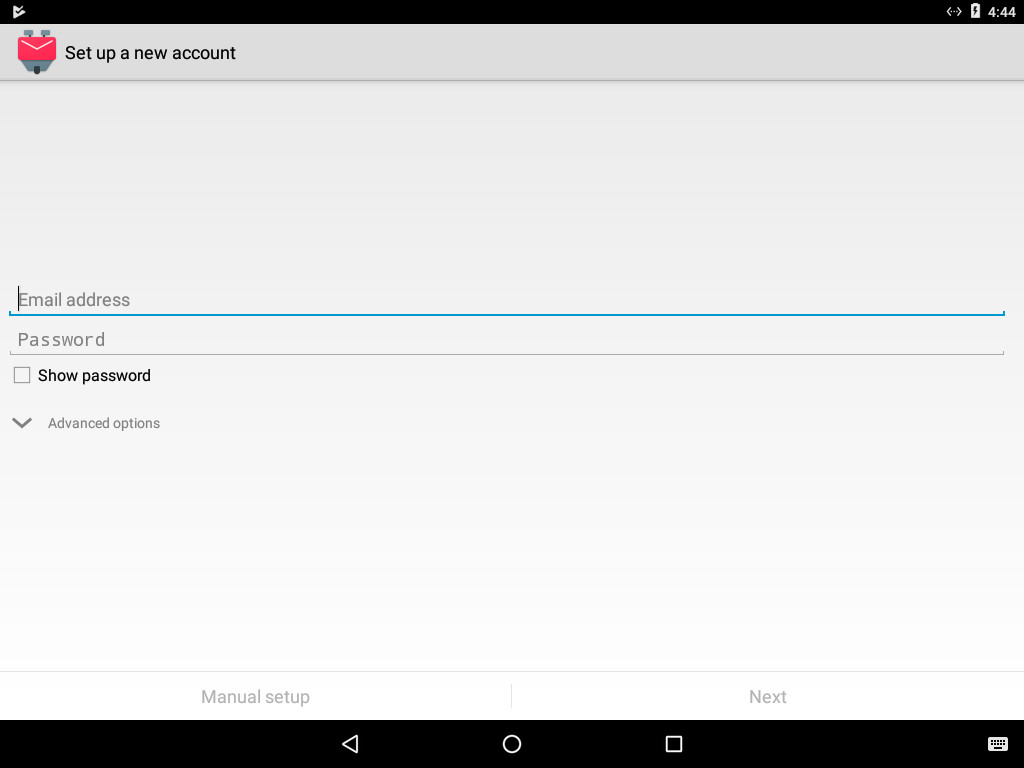
2) On the next screen, enter your full email address and password, and select “Next”.
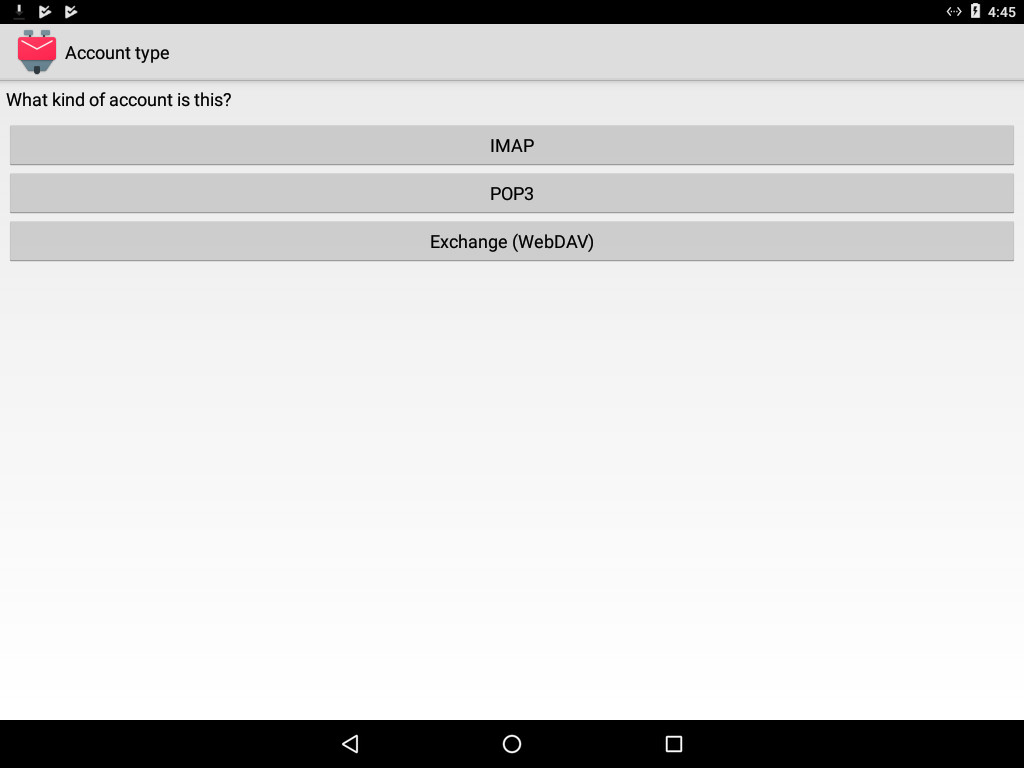
3) Select “IMAP”.
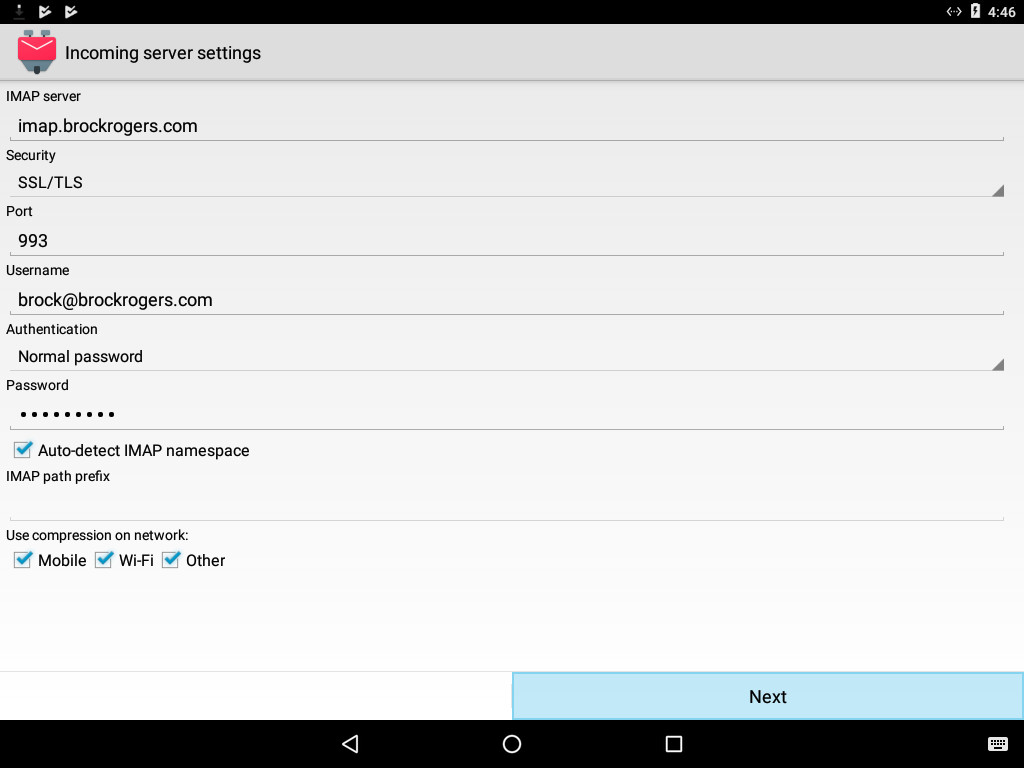
4) The settings on this screen should fill in automatically, but if they don’t, fill in:
- IMAP Server: imap.[yourdomainname.com]
- Security: SSL/TLS
- Port: 993
- Username: [your full email address]
- Authentication: Normal password
- Password: [your password]
Then select “Next”.
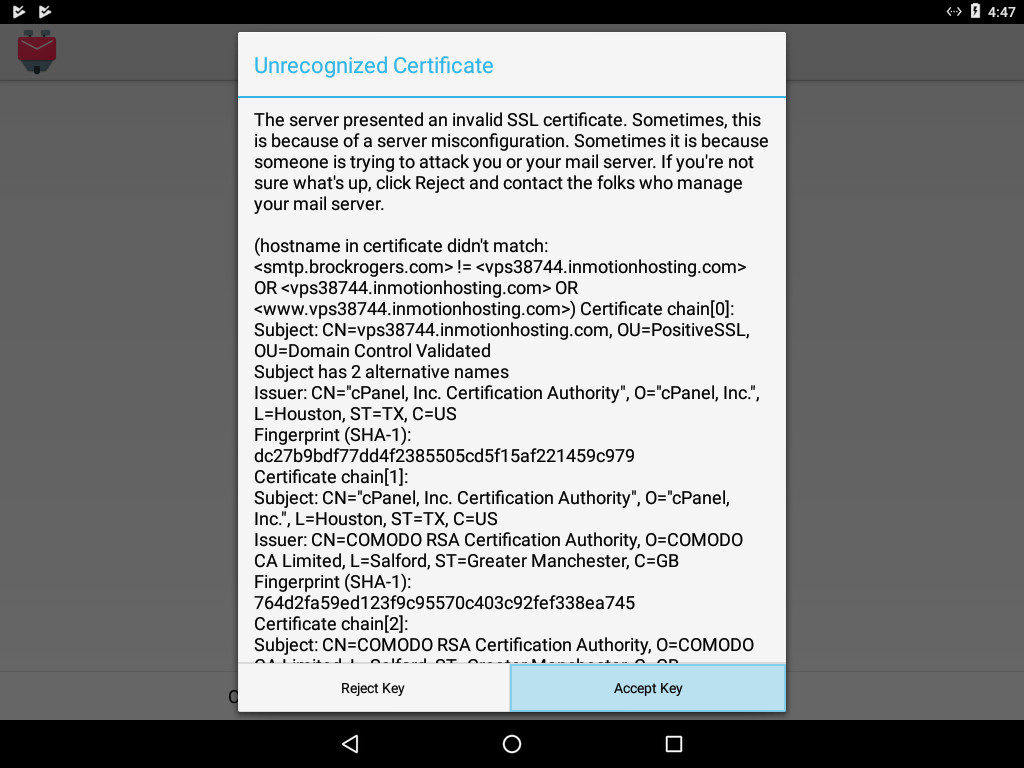
4a) If presented with this screen, select “Accept Key”.
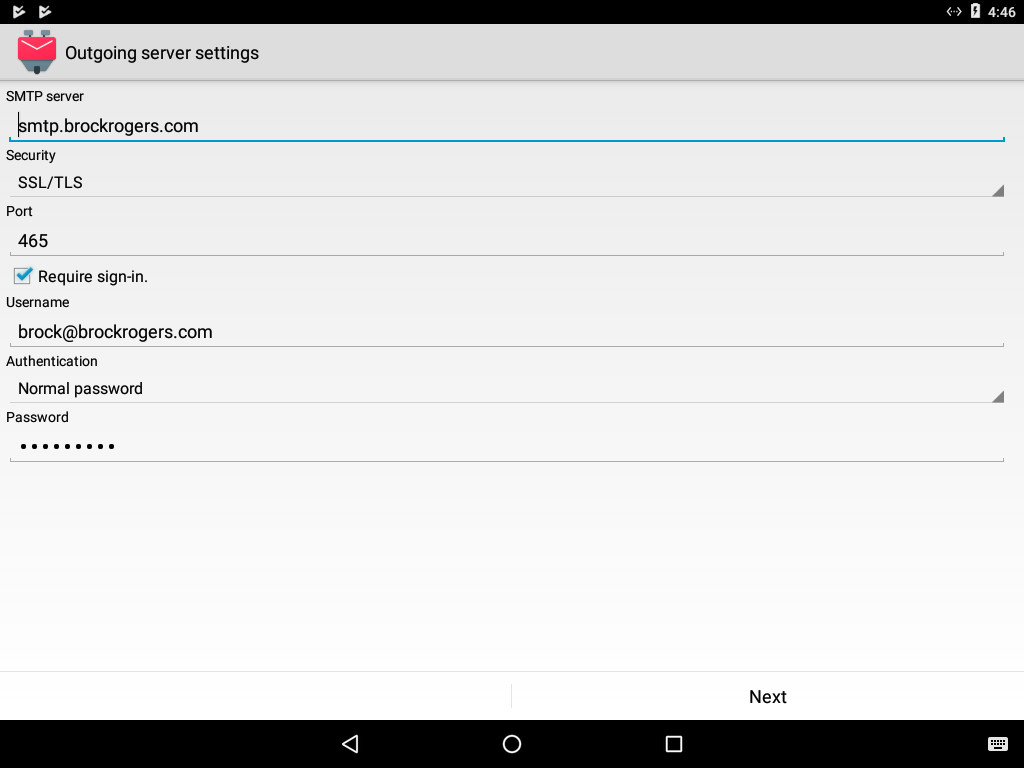
5) The settings on this screen should fill in automatically, but if they don’t, fill in:
- SMTP Server: smtp.[yourdomainname.com]
- Security: SSL/TLS
- Port: 465
- Require Sign-in: Checked
- Username: [your full email address]
- Authentication: Normal password
- Password: [your password]
Then select “Next”.
5a) If presented with this screen, select “Accept Key”.

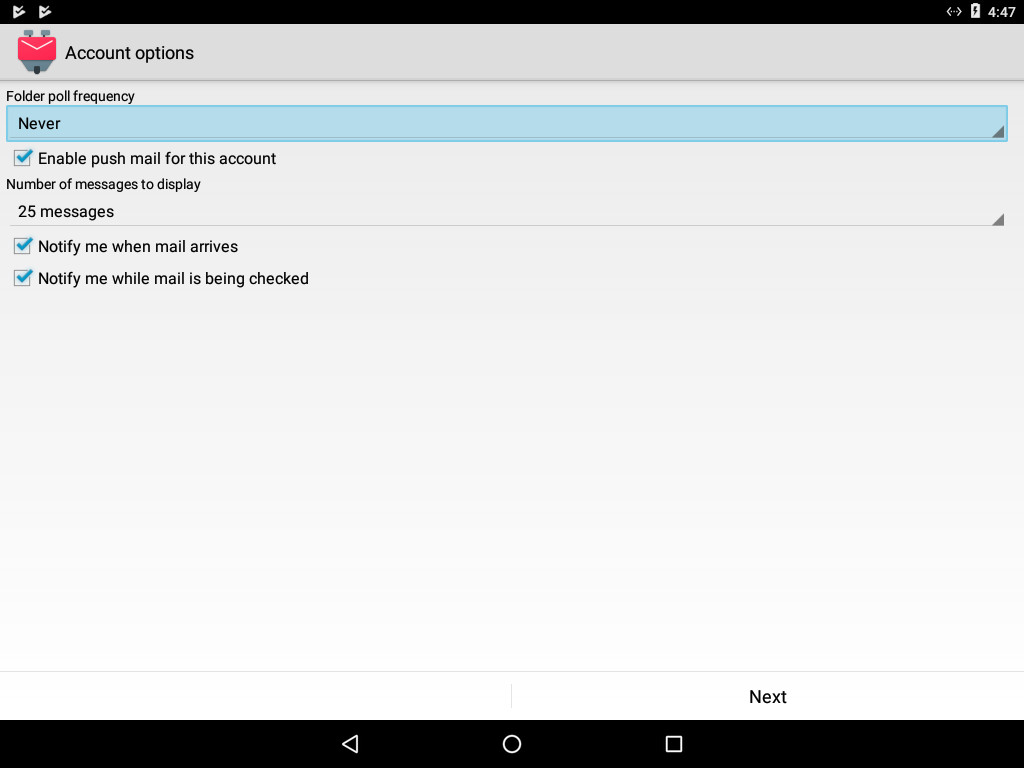
6) The settings on the following screen should all be correct, unless you tend to have a lot of email. If that’s the case, you can change the “Number of messages to display” to a higher number.
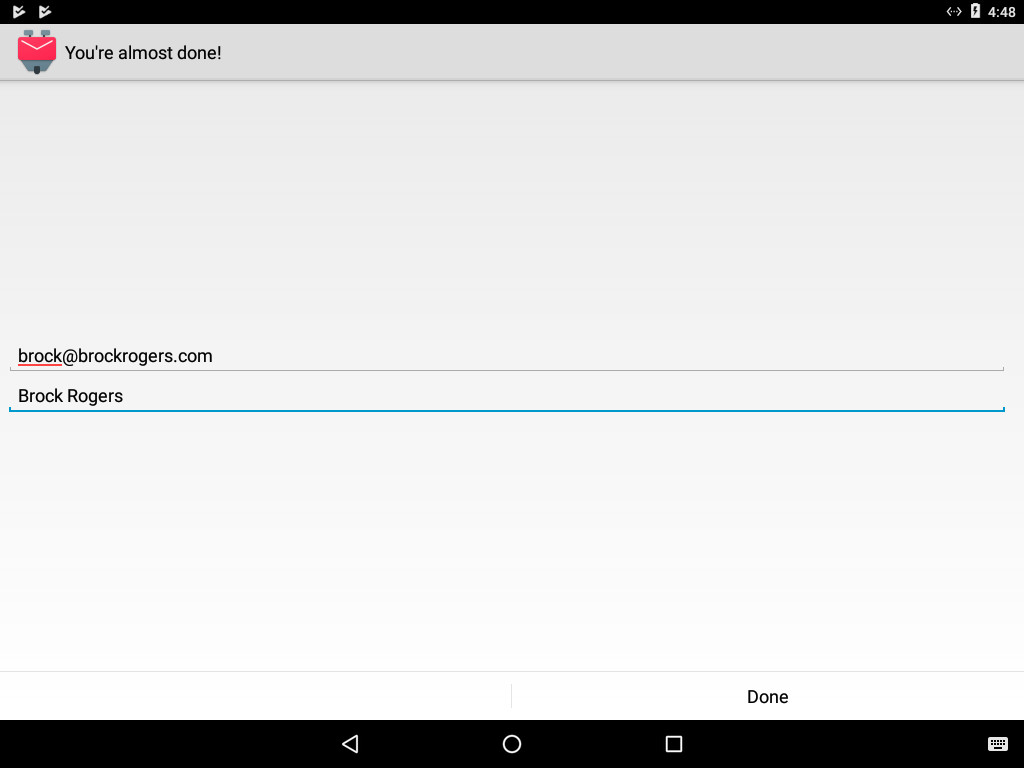
7) Finally, retype your email address in the first field, and your name in the second field. Note: The name you type in the second field will be used on emails you send.
10 Must-Have WordPress Plugins

One of my favorite things about WordPress is how extendable it is. As I’m writing, there are currently 43,739 plugins available in the official directory, and, if you can’t find what you’re looking for there, you can always make it yourself. So, what plugins do we think are must-haves? Here’s our pick of 10 of them.
Jetpack
No self-hosted WordPress installation is complete without Jetpack, which brings all sorts of WordPress.com features to your personal blog or company website. You can build custom contact forms, display your portfolio, keep track of site’s stats, and automatically connect to the most popular social media sites. And that’s just a few of the 35 or so features Jetpack has to offer.
All In One SEO Pack
When they say ‘All In One,’ they really mean it. AIOSEOP is the Swiss Army Knife of SEO plugins, and allows you to manage individual posts, pages, and even custom post types. It also lets you verify your site with Google’s Webmaster Tools and Bing’s Webmaster Central, add the Google Analytics code to your header, and even build XML sitemaps for submission to search engines.
Yoast SEO
So, if you feel confused by all of the options the All In One SEO Pack has to offer, then Yoast SEO is the plugin for you. While the first focuses on those who already have a good grasp of Search Engine Optimization, Yoast is much more friendly to those still learning about SEO, and includes a powerful page analysis tool to help you write better content, and make your site more friendly to search engines.
Wordfence
It isn’t a secret that WordPress is frequently targeted by people wanting to do bad things; that’s what happens when you’re the most widely used content management system. While there are many security plugins out there, Wordfence is our choice, because it’s powerful and, once configured, will take care of most issues before you even get the chance to check on them.
BackWPUp
There are almost as many backup plugins as there are opinions on which WordPress backup plugin is the best. Our choice is BackWPUp, because it’s easy to configure (even for those not that technically inclined), and can store your backups on remote FTP servers, Dropbox, have them sent to you via email, and many more.
Akismet
Another great plugin by the folks that brought you WordPress in the first place. Akismet helps keep your blog spam free by running any new comments through their servers, and automatically marking the spammy ones as spam. It requires an API key, but for personal blogs, it’s free, provided you have fewer than 50,000 comment attempts a month. For a professional account, the cost starts at just $5.
WP Super Cache
One of the drawbacks of using WordPress is that serving the complicated PHP files takes more time (and more server resources) than a static HTML file. WP Super Cache takes some load off of your server by building a static HTML file for the dynamic PHP pages. Once a period of time of your choosing passes, the static page will be dropped and refreshed. It’s a good compromise between static and dynamic.
WP-Optimize
It happens to the best of databases: over time, they gather extra lines of information that will never be useful again, causing them to slow down bit by bit. WP-Optimize takes that less-than-perfect database and cleans it back up again, improving performance, reducing space, and keeping WordPress generally happy.
Safe Redirect Manager
Posts and pages sometimes come and go, leaving search engines guessing as to where to go when it can’t find something. Safe Redirect Manager gives them a bit of direction, in case you move, or completely remove, anything from your website.
WordPress Importer
OK, WordPress Importer isn’t something we keep installed on all of our WordPress sites, but it’s one of those that, when you need it, you really need it. It allows you to take a WordPress export file, and pull all of the posts, pages, categories, tags, and media files (or basically anything you need) into a new WordPress installation. Great for when you need a sandbox to test out theme or plugin development.
Well, there you have it: our 10 must-have WordPress plugins. What plugins do you find the most useful?
How DNS Works
 In the world of the Internet, computers don’t really have names. They have IP addresses, like 198.1.74.213 or 2001:4860:4860::8888. The problem with that is, people have a hard time remembering numbers, but we’re really good at remembering names. The solution is the Domain Name System, or DNS. DNS takes a domain name, like 10twebdesign.com, and resolves (translates) it to an IP address, such as 198.1.74.213.
In the world of the Internet, computers don’t really have names. They have IP addresses, like 198.1.74.213 or 2001:4860:4860::8888. The problem with that is, people have a hard time remembering numbers, but we’re really good at remembering names. The solution is the Domain Name System, or DNS. DNS takes a domain name, like 10twebdesign.com, and resolves (translates) it to an IP address, such as 198.1.74.213.
So, what really happens when you type 10twebdesign.com into your web browser and press enter?
Maybe I Already Know Who That Is
First things first, your web browser might already know where 10twebdesign.com is located, because you may have visited it recently. If you have, your browser will cache (remember) the information for a certain period of time, so it doesn’t have to keep looking it up if you visit several different pages in a row. But the first time you visit a 10twebdesign.com page, your web browser has no idea where 10twebdesign.com is, so it starts the processes of trying to find out.
Let’s Ask Around
So your web browser tells your operating system, “I need to know where 10twebdesign.com is.” It’s possible that your OS already knows, and will just tell your browser, but chances are, it doesn’t know either. What it does know is the address of a preferred DNS server, which is usually owned by your Internet service provider and assigned automatically. So, your operating system heads out to your DNS server to find out where 10twebdesign.com is located.
Your DNS server handles requests from basically everyone in your area that all use the same Internet Service Provider that you do, so it’s much more likely that they might already know where 10twebdesign.com is, and can answer straightaway. Still, it’s more likely that no one has looked it up recently enough, and the DNS server needs to find out, too.
Going to the Source
Your DNS server will now start working backwards; it needs to find out who manages the ‘.com’ domain names. Chances are, it already knows the answer to that, because someone else has recently looked up some other .com domain name, and it would have cached the information, but for the sake of this article, let’s say it doesn’t know and needs to find out.
Your DNS server now resorts to asking a root name server, of which there are only 13 in the world. These servers, named with the letters A – M, are located all over the world and are owned by many different organizations, including NASA, the University of Maryland, and the U.S. Army Research Lab, just to name a couple. Everybody knows where these 13 root servers are, so they can always fall back on them when everything else fails. Your DNS server tells one of the roots, “Hey, I need to know who manages .com addresses,” and the root server responds, “It’s Verisign.”
You DNS server now caches the information from the Verisign server, so that next time someone looks up a .com domain name, your DNS server won’t need to bother the root servers; after all, they are pretty busy, and it would make more sense to just remember and go directly there. It then heads over and asks the Verisign server, “Can you tell me who knows where 10twebdesign.com is?” The Verisign server responds with “They are registered through this domain registrar.”
So, your DNS server now heads over to the domain registrar, and says, “I need to know the name servers (NS) of 10twebdesign.com.” The registrar responds with one of two or more servers that know where 10twebdesign.com is actually located.
At last, we know who to ask. Your DNS server now makes direct contact with one of 10twebdesign.com’s NS servers, and asks, “Where is 10twebdesign.com located?” Our NS server replies, “It is located at 198.1.74.213, and it has a TTL of 14,400 seconds.” Your DNS server takes this information, and caches it so that the next time someone looks up 10twebdesign.com, it can just tell it the answer of 198.1.74.213, and save a whole bunch of work.
Great, Now Everybody Knows
The only issue with this is that it’s possible that 10twebdesign.com might move at some time in the future. That’s where the TTL, or Time To Live, comes in. So, for the next 14,400 seconds, or four hours, you can find 10twebdesign.com at 198.1.74.213. After that, it might change. So, when your DNS server caches the information for 10twebdesign.com, it sets it to expire after the number of seconds specified in the TTL; once it expires in your DNS server’s cache, it will have to look up the information again.
Last, but not least, your DNS server returns the address of 10twebdesign.com to your operating system (that caches the information for the same length of time), and your OS passes the information along to your web browser (which also caches the information), so that it can look up the website hosted there.
The most amazing thing is that, if everything happens as quickly as it should, all of this happens in about a tenth of a second. Now that’s fast.
Sheriff’s Office ‘Wanted List’ Featured
It’s a pretty good day when you see something you created featured in the local news:
The Belmont County Sheriff’s Office is unveiling the county’s ‘Most Wanted’ list.
Sheriff Dave Lucas implemented a new feature on their website – a place where you can easily find who’s most wanted.
“Just go to belmontsheriff.com. Go over to the information tab, and you’ll find the wanted,” Lucas said. “And you’ll see a list of wanted people you’re looking for, and we’ll keep adding to that.”
The Wanted List is powered by a WordPress plug-in created by 10T Web Design specifically for the Belmont County Sheriff’s Office. It allows officers to add pictures and basic information for people on their wanted list directly to their website, without the need to know anything about designing web pages.
It is one of several plug-ins we’ve created for their website, which we also design and help manage. Others allow them to list properties for their monthly Sheriff Sales and help to keep the people of Belmont County aware of the winter road conditions, both of which are managed by members of their staff.
Looking forward to continuing to work with the Belmont County Sheriff’s Office, who have been a client of 10T Web Design almost since we came into being.